Every reverse engineer, malware analyst or simply a researcher eventually collects a set of software that they use on a daily basis to analyze, unpack, and crack other software.
This article will serve as an index of software I collected, you could need, so you don't have to hunt for them on your own. It will be useful to anyone who has not yet collected their own set of tools and is just starting to look at the subject or people who want to extend their current set of tools.
First, some Definitions and Clarifications:
Debugger:
A Debugger is a software tool which allows the user to view and change the running state of a program.
Disassembler:
A disassembler is a software tool which converts binary to assembler which is a bit more human-readable code.
Decompiler:
A Decompiler is a software tool which reverses the operations of a compiler and converts binary or intermediate code to the (near) original source code.
Debugging the assembly code output of a Disassembler is the answer to everything (Besides 42). By debugging the assembly you are able to reverse engineer EVERY program there is because you can see exactly what the CPU is going to do. No matter how well obfuscated it is or if it's an Interpreter, Jiter or Compiler language.
Debugging the output of a Decompiler on the other hand is mostly specialized on one specific programming language or framework which makes them not the answer to everything and that is why i gave them their own section.
I also put Debuggers and Disassemblers / Debuggers and Decompilers in the same section because most disassemblers and decompilers also include a debugger - So I don't see a point in splitting these up for this list.
With that out of the way.. Lets get into the List.
Debuggers / Disassemblers
X64dbg
X64dbg was a much-needed innovation. It's pretty easy to use, and the features were worth a wait. It has been the strongest tool on the market in the Debugging Department. This is a new debugger with a decent user interface, a worthy successor to the older OllyDbg that everyone used before. It supports both architectures (x64 and x86) and there are lots of useful plugins available.
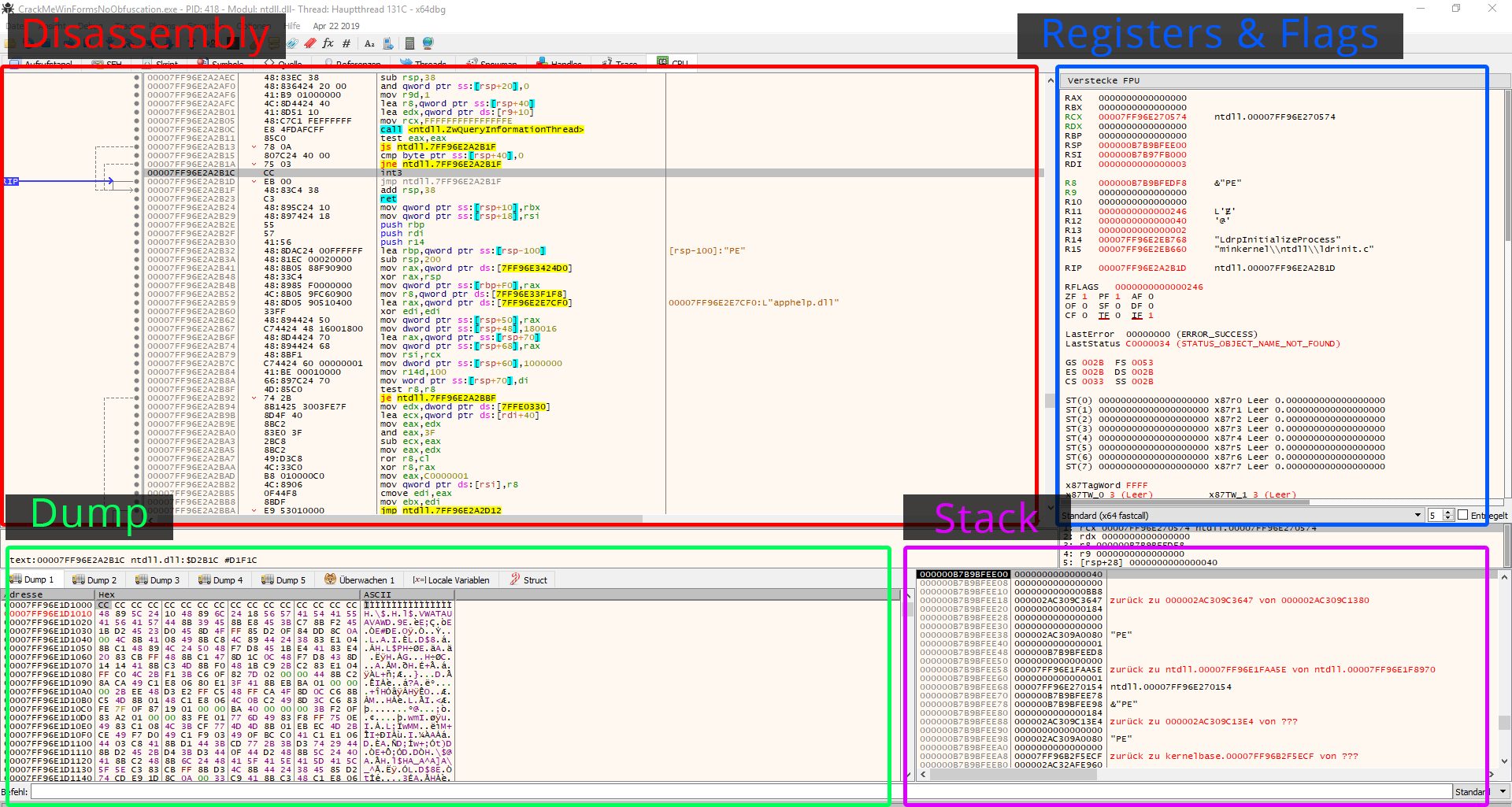
Granted, it's got its downsides, since there may be some bugs. But it is being actively developed and supported. Of course, because the debugger operates in user mode, it is vulnerable to a wide variety of anti-debugging techniques. However, this is partially compensated by the availability of several different debugger hiding plugins.
X64dbg also provides a built-in decompiler and import reconstructor (both x64 and x86), supports code graphic visualization and read/write/execute/access breakpoints.
IDA Disassembler
The IDA Pro disassembler is a de facto standard in antivirus laboratories.
There are two versions of IDA, a paid Pro version and a free Starter version. The free version is limited to x86 and does not support plugins. The Pro version offers full functionality with many supported processor architectures and plugin support.

IDA has a built-in debugger with rather basic functionality and can also be augmented with the Hex-Rays add-on, a decompiler of application source code into C code. This is very useful as it really speeds up program analysis.
Overall, IDA is a very strong and polished tool with a long history of development. Unfortunately, the paid edition costs between $365 - 2000+ depending on the type of license, and they don't sell it to everyone.
Qira
Qira is a timeless debugger made by the ever-popular or hated (whatever site you're on) geohot who is quite famous for jail breaking the iPhone and PlayStation 3 and then getting into legal trouble for it.
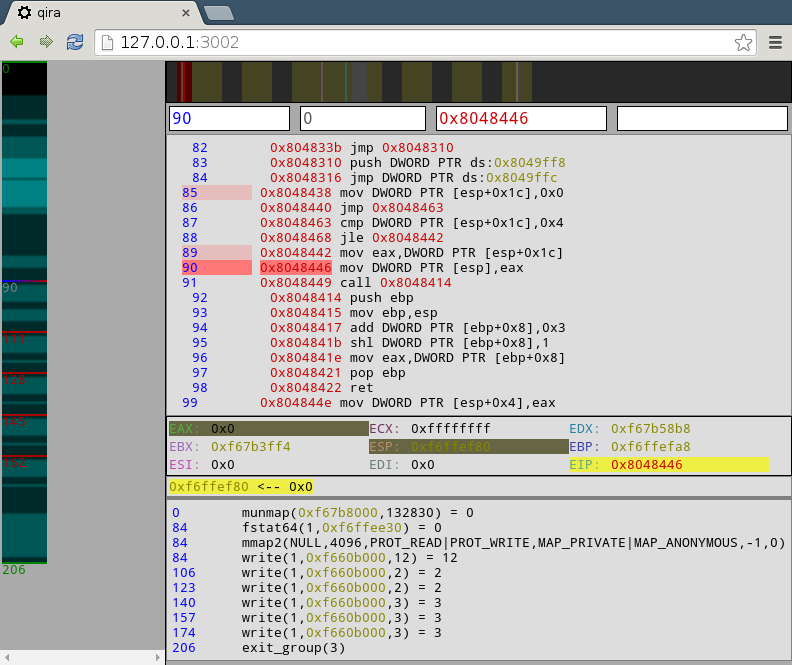
What made this debugger special when it came out is the way you could reverse your steps if you did something wrong.
Other debuggers also had that option, but they did it "wrong" because the program wasn't exactly the same as before your steps and programs were able to detect that.
Qira changed this by using a similar strategy Git uses. It saves the steps you did in a tree like structure, and if you want to reverse a step, it loads an older "save file" of the program. Saving all of these save states takes a lot of computing power, of course, but modern computers are so powerful that it really should not be a problem.
This tool is open source and actively being worked on, but due to its "young” age and it being less popular, which leads to fewer people working on it, it can have quite a lot of bugs.
The debugger itself runs in a browser which makes this program available on Windows, Linux and Mac.
Ghidra
More "recently" (since 2019) Ghidra, a NSA suite of tools (So not only a Debugger), has been released. Yes, THE NSA. They even got a GitHub Profile.
It's being actively developed and probably even used in house by the NSA because the version you can download is known as the "public" version - that is why there's probably a "private" version as well.
Ghidra is able to disassemble, assemble, decompile, graph, support Java/Python plug-ins and/or scripts, has an auto-analysis feature (which can sometimes be very slow) that could certainly help you with your work, currently supports more than 30 types of processors, plus hundreds of other features.

If you're used to IDA or the like, it might take you some time to get used to Ghidra, but when you get used to it, it will become very useful in your toolkit, despite the initial bugs it has due to its younger age.
You can get Ghidra from the NSA’s official page for Ghidra here or get the whole source code from their GitHub here.
Debuggers / Decompilers
.NET
dnSpy
dnSpy is a tool to reverse engineer .NET assemblies. It includes a decompiler, a debugger and an assembly editor, and more and can even be extended by writing your own extension.
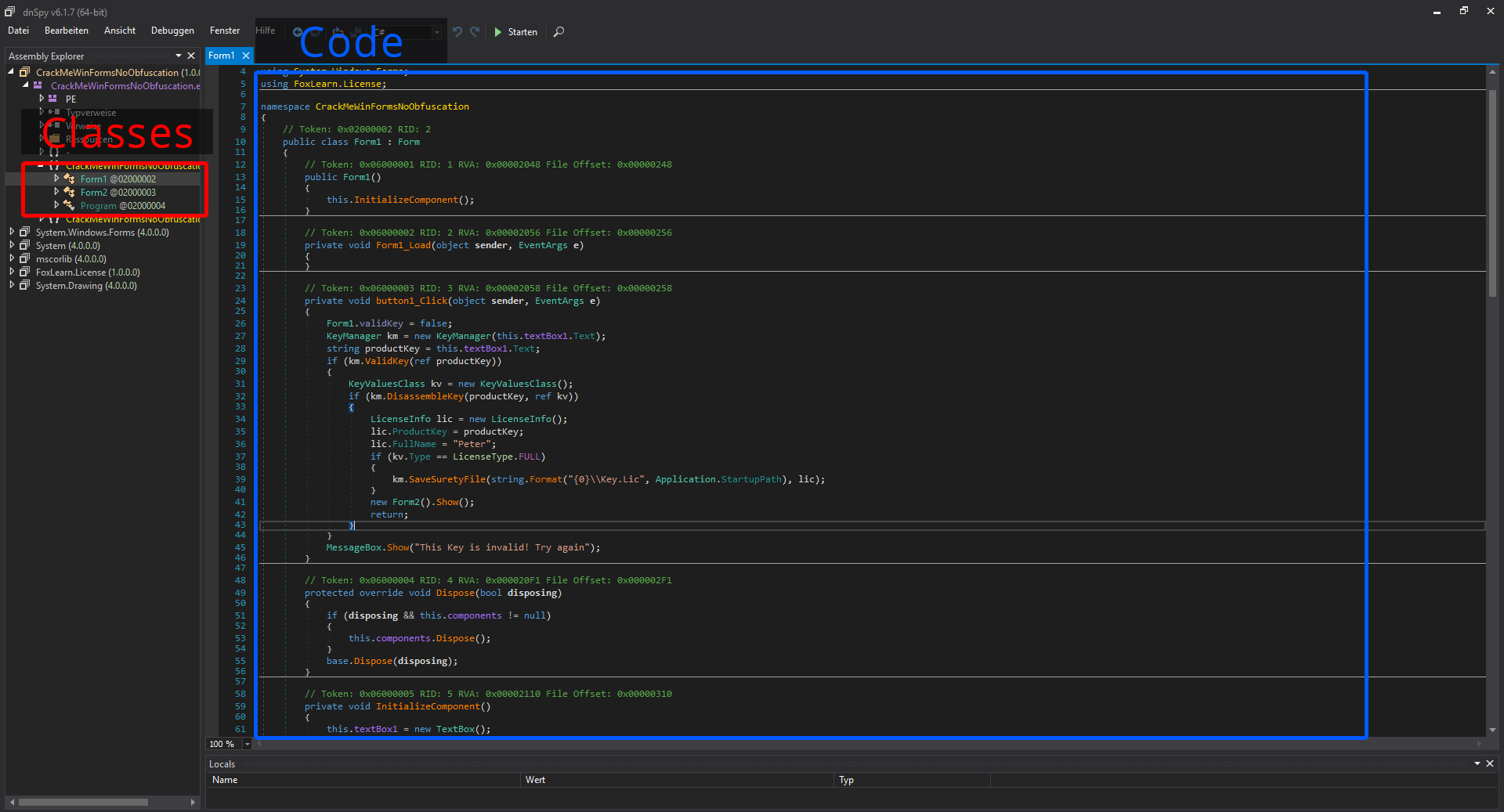
dnSpy does not output assembly code and does not Support all programming Languages Like the X64dbg I talked about above.
It only focuses and outputs .NET Programming Languages like C#, F# or Visual Basic.
That makes it not so useful for most viruses and the like but a lot of more user oriented desktop Programs that are written in C#, which makes it quite useful for those.
There are also tons of other .NET decompilers like JustDecompile or dotPeek, but they don't let you edit the code right there, they just let you see it - that is why all in all, dnSpy has been my go-to for .NET programs (If you want to find out if a .exe is even a .NET file, read further and ill talk about a program that is able to do that)
Networking
Fiddler
Telerik's Fiddler is a web debugging proxy application that logs all HTTP(S) traffic between your computer and the Internet.
This may be useful if you want to see if a Virus/Program connects to a certain website or similar, to send data that you may be able to inspect, intercept, alter or otherwise fiddle around with.
Fiddler provides an easy-to-use interface that makes it clear where your requests need to be entered, as well as the request body and authentication information (among other things). It's also very convenient to see your past requests and past results.
They're all present on the same page, which is good because you don't have to navigate to different pages or similar.
But its capabilities are very limited. It doesn't have a lot of features outside of basic REST requests that run one at a time. You will need to manually type all REST requests with the exact perfect syntax instead of having them done in a more automatic way.
But in general, this is one of the most valuable tools for any hacker.
TCPView
Microsoft’s TCPView would be a lightweight alternative to Fiddler - It is a very limited but also very lightweight (< 300KB) network monitoring software that is also part of the SysinternalsSuite.
You can see process identifiers, the ports it accesses, protocols and packet counters.
Postman
This is again an alternative to Fiddler and TCPView, but it specializes in websites and your browser instead of all programs on your computer.
I still included it in this list because you might be trying to reverse engineer some web app, or your desktop app might interact with some web API you found using Fiddler or TCPView, and now you need to reverse engineer that.
Postman is a browser add-on (currently only available for Chrome) that, along with the desktop app, allows you to intercept, save and filter requests with your cookies to be inspected and sent later.
This way, you can quickly reverse engineer an API to see how it functions and how you can control it.
It's mostly focused on developers and not hackers, but it has still become a commonly used tool in my toolkit whenever I need to check out an API.
Wireshark
Wireshark is a free network analysis software that was created as an Ethereal fork in 2006 that lets you see what applications send and receive from the Internet, monitor network activity, find hidden communication channels and more.
It's probably the most powerful network analysis tool, and it's a real Swiss Army knife - It captures all kinds of packet data of the network, displays packet direction and path, displays errors and issues below the HTTP protocol, and has a great filter and search function.
Unfortunately, it misses the ability to change and manipulate things on the network and can sometimes show too much information that can overwhelm you (which could be fixed by a better UI?).
Packer Detector
ExeInfoPE
While conducting malware analysis, I considered Exeinfo PE to be an invaluable tool. Exeinfo PE is a lightweight packer and protector detector.
Exeinfo PE has an unorthodox interface that is not to everyone's tastes, but is somewhat reminiscent of the now unsupported PEiD that many analysts still use, but unlike PEiD, Exeinfo PE is actively developed and maintained.
Exeinfo PE is good at telling you most of the information you care about up front, and it also tells you what you should do next, including telling you to use another detector, run an advanced scan, use Ida, use OllyDbg, and so on, and has most of the features analysts are asking for.
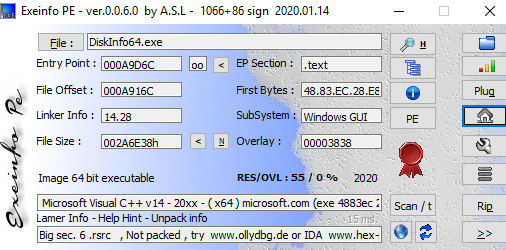
However, just like other analysis tools, Exeinfo PE has its downsides. It's not going to be your one-stop file analysis tool - I don't think there's any tool ever going to be, at least for malware. ⠀
One place where Exeinfo PE fails is not detecting older packers and protectors, as the author notes on their website, but you could use PEiD for this task.
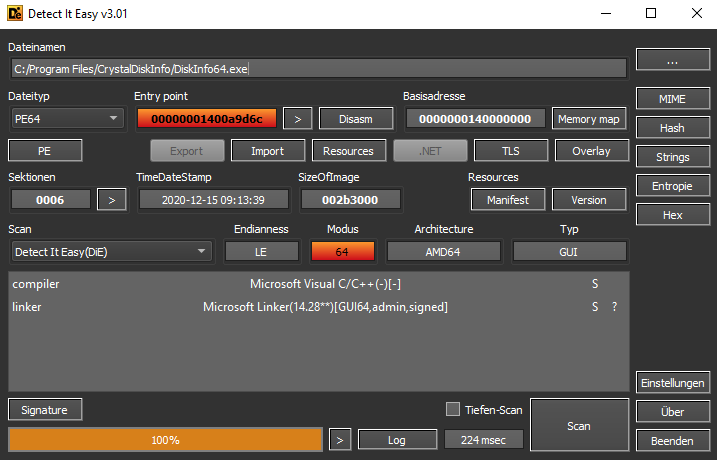
Detect it Easy (DiE)
This is a great packer identifier with a variety of useful functions and is designed with an open signature architecture and allows you to build and incorporate your own detection algorithms.
It also allows you to access the entropy portion of the file, which enables the visual recognition of encryption.
It also has a resource viewer with a dump-to-disc functionality. DiE allows you to quickly access the import table and add plugins and scripts, customize signature scanning methods, and view file headers. It completely supports both PE and PE+.
Pestudio
PEstudio is a very interesting tool. In addition to bringing the basic features you would expect from a PE analysis tool, PEstudio also attempts to decide if a file is malicious on the basis of some indicators it might have and automatically scans file samples with VirusTotal, provides an interesting view of the import table functions of the analyzed program, displays the application's viral markers, used libraries and PE file header info.
To give you an idea of how these indicators operate, assume, for example, that a file you are monitoring contains version information relevant to a Microsoft file. However, the same file is obviously not from Microsoft, so PEstudio will let you know about this difference.
The details given by the indicators can often be useful if you are already suspicious of a file. In certain cases, the knowledge you get is sufficient to solve your issue, but in any case, it will give you a good starting point.
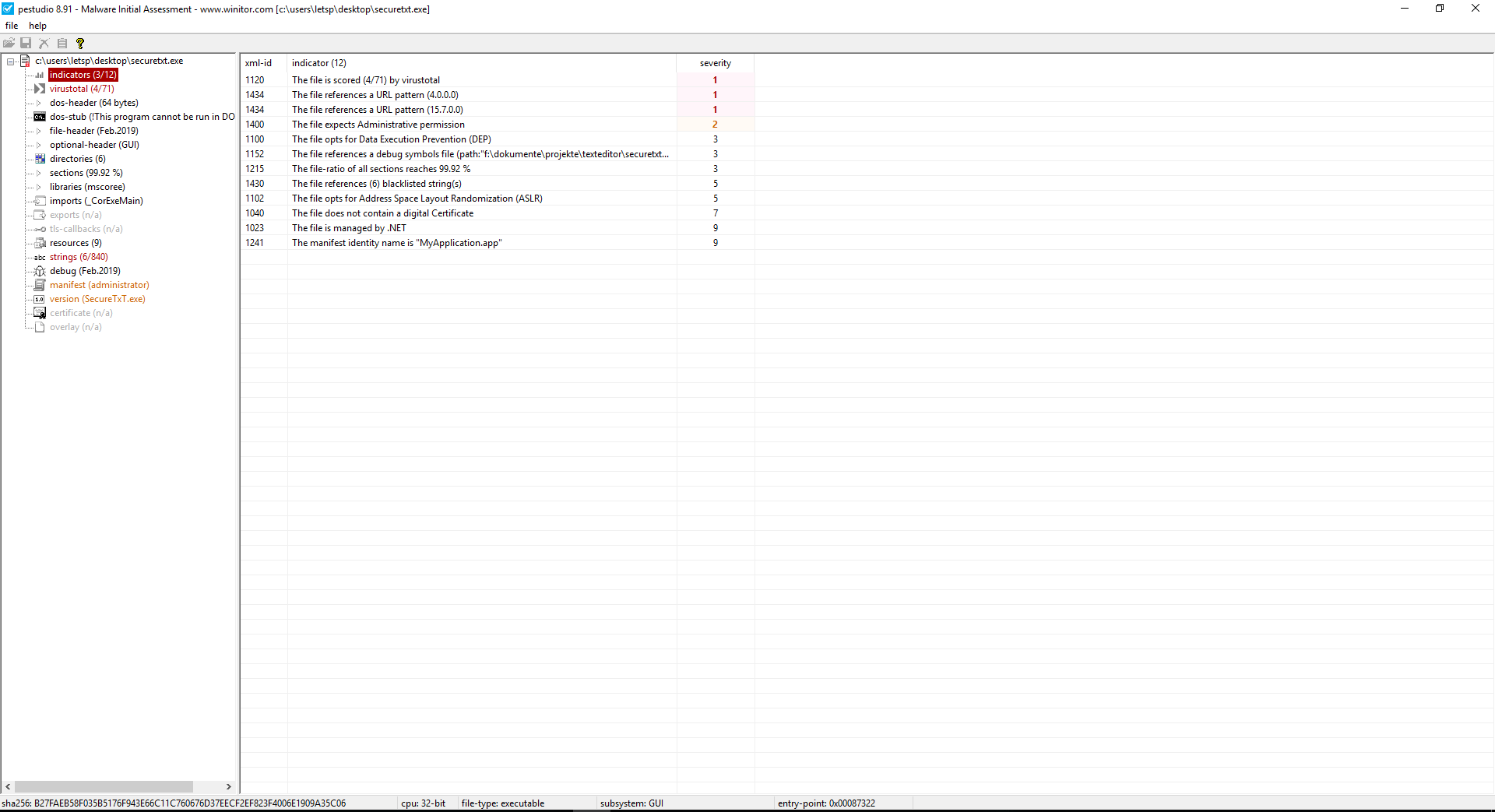
While PEstudio is a great program, the GUI is a tad empty, and sometimes the indicators are of limited use when dealing with specially designed binaries. However, if your final target is a program that works hard to classify a file as potentially malicious, PEstudio is a powerful antivirus tool for initial sample review.
File Viewers
HxD
Sometimes you may need to access HDD, memory or applications in binary mode.
This is where hex editors such as HxD come in handy which is free of charge for private and commercial use.
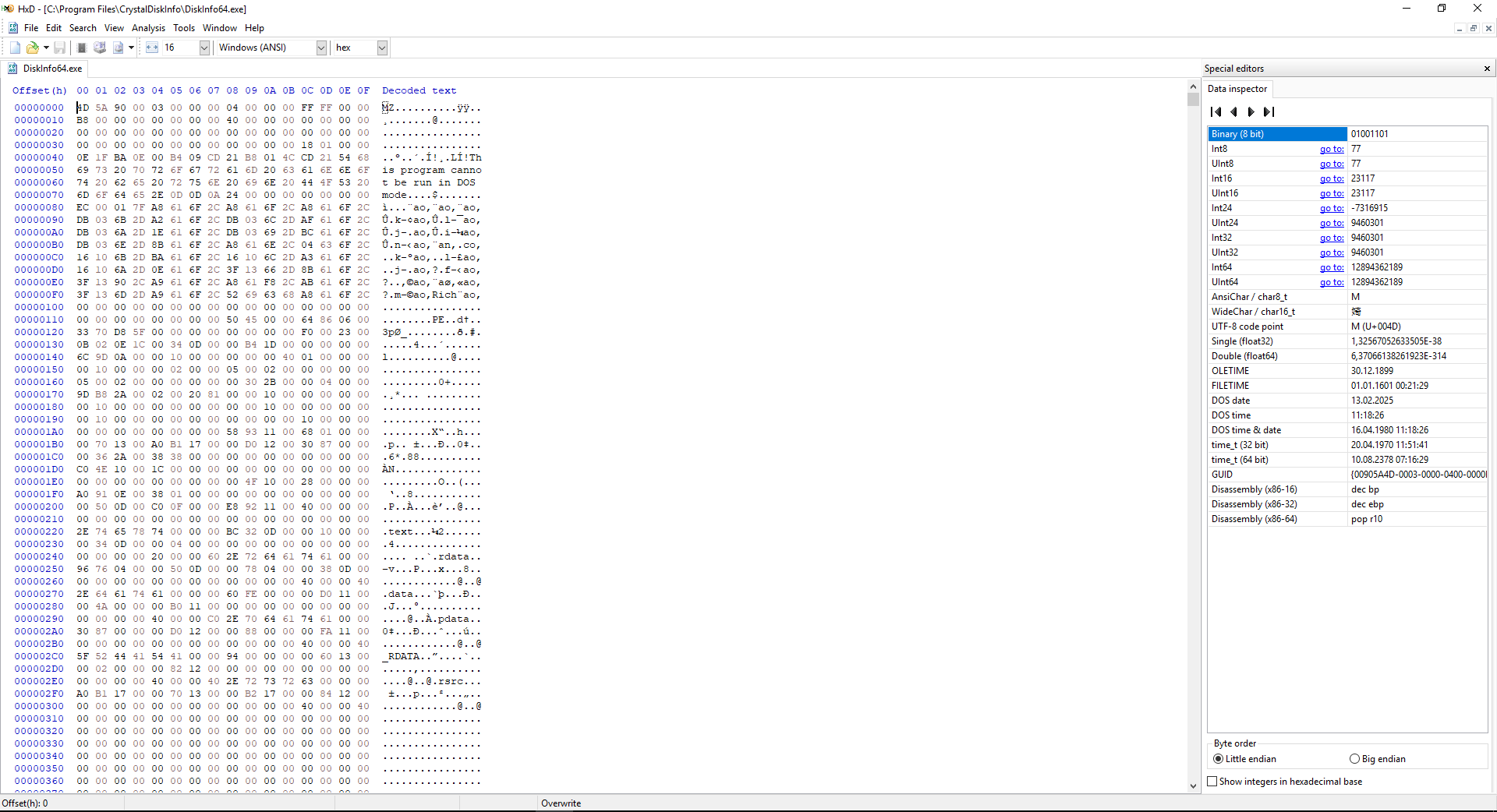
Often updated, this program is a Windows hex editor that can handle files of any size, can be used as a RAW disk editor and RAM editor, supports common formats, and provides a user-friendly UI.
There are other features that are well executed, such as the ability to remotely clear files (zero fill), checksums, exporting, insert byte patterns, file splitting, statistics etc.
If you don't want or can't install this application on your machine, there's also a portable version that's always handy.
LTFViewr5u
This is another tool where you might argue that it doesn't belong to this list, but I'm still adding it here because it's very useful, and it took me a week to find it when I needed it initially.
The Large Text File Viewer is designed to view verrryyy large text files. It uses little memory and is able to open very large files (>5GB) instantly. Background file indexing makes searching easier. It also helps the user to do a high-speed, complex text search using plain text or regular expression.
If you've ever tried to open large text files, you'll probably reach the limits of the standard Windows Editor fairly quick, and if you've ever tried to open very very large files, you'll probably also find the limits of Notepad++.
I tried multiple of those supposedly "Large Text File Viewers" but most of them had a cap of 1 GB or 5 GB or something like that - LTFViewr5u, on the other hand, had no problem opening my 9 GB text file, and if I had a larger text file, it would probably have no problem opening it.
Resource Hacker
Resource Hacker is both a resource compiler (for .rc files) and a decompiler - allowing to access and modify resources in executables (.exe, .dll, etc) and compiled resource libraries.
It's very popular for editing resources, including manifests, text dialog lines, icons, cursor data, etc. You're not going to need this tool very often, but when you do, this is probably the best tool for the job.
Virtualization
Your reverse engineering job may require you to run some unknown, potentially hazardous code, such as malware. That's why you need a second PC or a Virtual Machine to not be afraid of damaging your PC.
Sandboxie
Sandboxie (or Sandboxie-Plus) is a sandbox-based isolation software for Windows. It creates a sandbox-like isolated operating environment in which applications can be run or installed without permanently modifying local & mapped drives or the Windows registry. An isolated virtual environment allows for controlled testing of untrusted programs and web surfing.
Normally, if you want to test a program quickly, you need to start a virtual machine which can take time and resources. Sandboxie lets you run just a program in a virtual environment.
You can do this by right-clicking on the EXE and clicking on "Open with Sandboxie" - This is quite useful for programs that you trust enough not to be a harmful virus which could break out of the Virtual Environment, but you still don't want to be running on your actual PC.
Just a few months ago, Sandboxie became Open Source, even though it's been tough since 2004, and it's split in two. There's a classic build with an old MFC UI (The one you can see in the screenshot above) and a new shiny Sandboxie Plus with a new Q't based UI.
Because Sandboxie just became Open Source so recently and is still VERY ACTIVE (the last commit was 10 minutes ago at the time of writing this, so that should say something), they still welcome new Volunteers. So if you want to work on some very well-known project for fun, or for your CV, this is your chance...
Other
ProcessExplorer
ProcessExplorer is known as the “better Task-Manager” - you can even make ProcessExplorer replace the normal Task Manager by following this Guide. It shows all processes in a hierarchical tree view, so you can quickly see their spawning order.
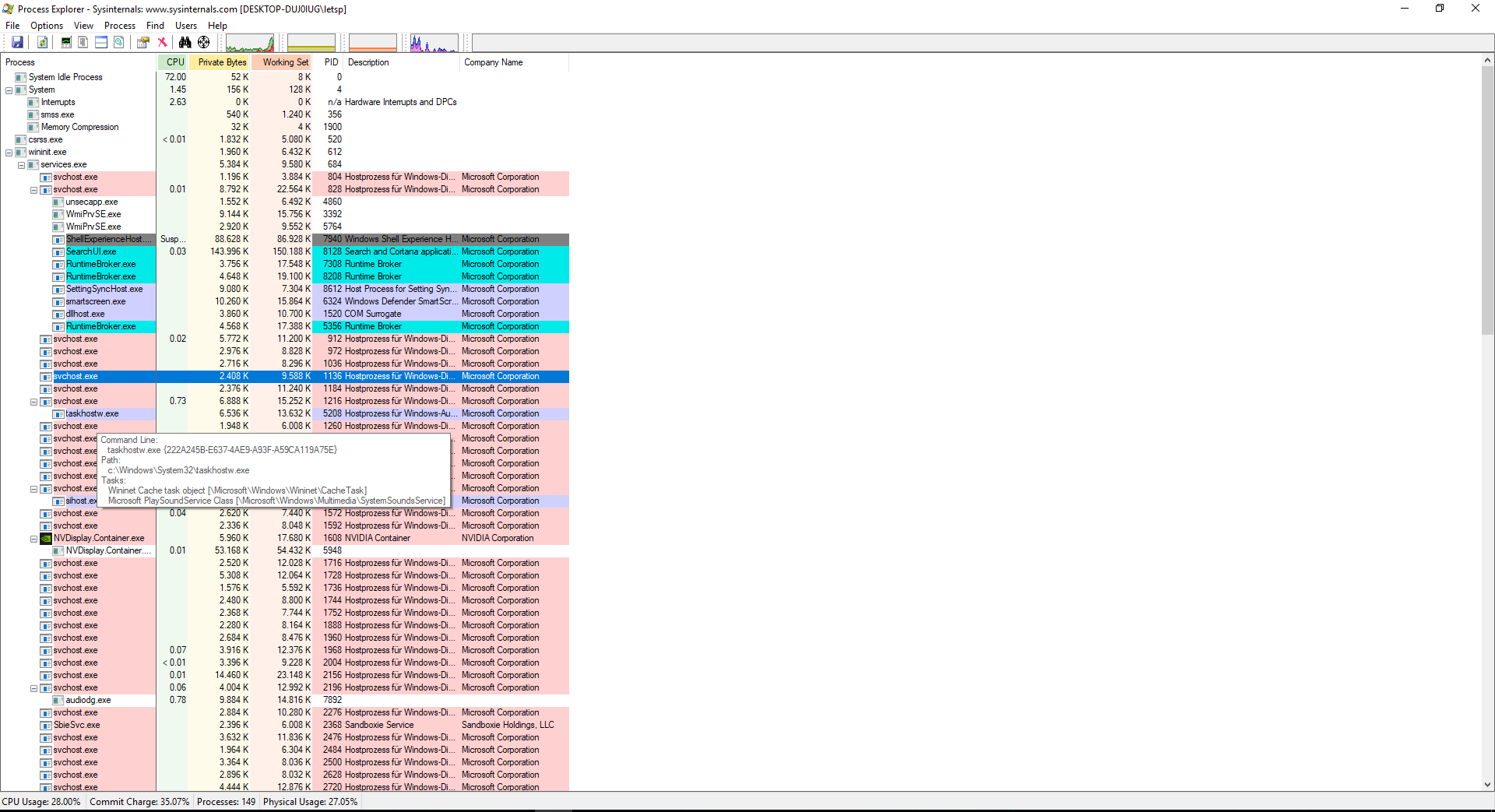
You can also see which application has a specific file or directory open, the libraries they use, as well as their priority, processor usage, digital signatures, and more.
RegShot
Regshot is a great utility that you can use to compare the number of registry entries that have been changed during installation or updates to your device settings.
RegShot takes snapshots of the registry before and after you make any changes to the system or through some potently malicious software you are trying to analyse.
Scylla

Scylla (Named probably after the legendary Greek monster)allows you to dump the process memory of a running application to a file which lets you see the unpacked version of a programs memory and enables you to do some more "juicy" (I read this exact wording on some forum a while ago) stuff with the program.
Furthermore, Scylla also integrates with x64dbg where it can be directly launched by clicking Plugins => Scylla, so it could be that you already heard and used Scylla.
SysinternalsSuite
The SysinternalsSuite is, as its name might already tell you, a suite of different tools (I partially already covered above) that are a must-have for any hacker.
I'm not going to go into the specifics of all the 70+ tools that it contains, but you can just download them and check them out or read about them here, where all the tools with additional information are listed, and find out which of them may be useful to you.